Introducing
Breach Assessment
Vulsan X Breach Assessment is aimed to create awareness to organization on the increasing number of cyberattacks occurring & the importance to be vigilant and be ready to respond to cyber threat. This Breach Assessment also be able to evaluate the state of Cyber Defense of the user’s network, as it provides a complete overview of the state of their organization vulnerability against the potential cyber attack which could create many potential damages.

- Detection & Analysis
- Containment/Eradication And Recovery
- Post-Incident Assessment And Audit
- Development of Breach Response Program
Comparison
Conventional Breach Assessment
• Obsolete technology
• Mostly tap/mirror or span port based solution
• SIEM software only Provide Detection of Threat no Action to Mitigate
• Manual monitoring and analysis by humans / SOC engineers
• Cannot mitigate sophisticated attack
• SIEM provide visibility not security
Vulsan X Breach Assessment
- Latest modern techniques
- Automatic detection and mitigation
- Operates in stealth mode, invisible to the attackers – NO IP or MAC
- Inline deployment
- Implements multiple security engines
- Can detect and mitigate even the most sophisticated attacks
- Mitigation on the RUN both ways in coming and Outgoin

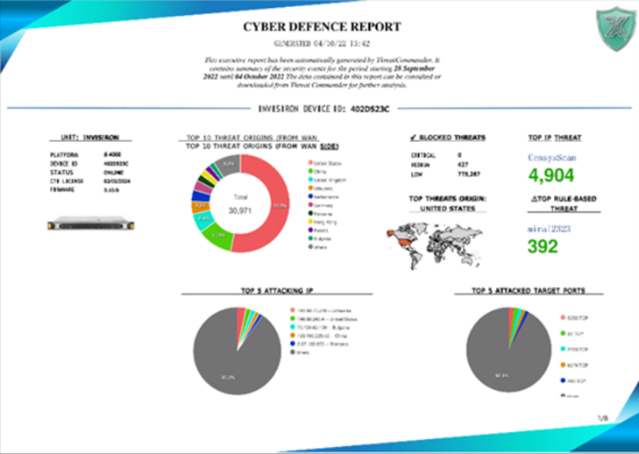
What you will gain: A comprehensive overview on RISK LANDSCAPE to understand where you should put FOCUS to mitigate CYBER RISK.
How Does It Work?
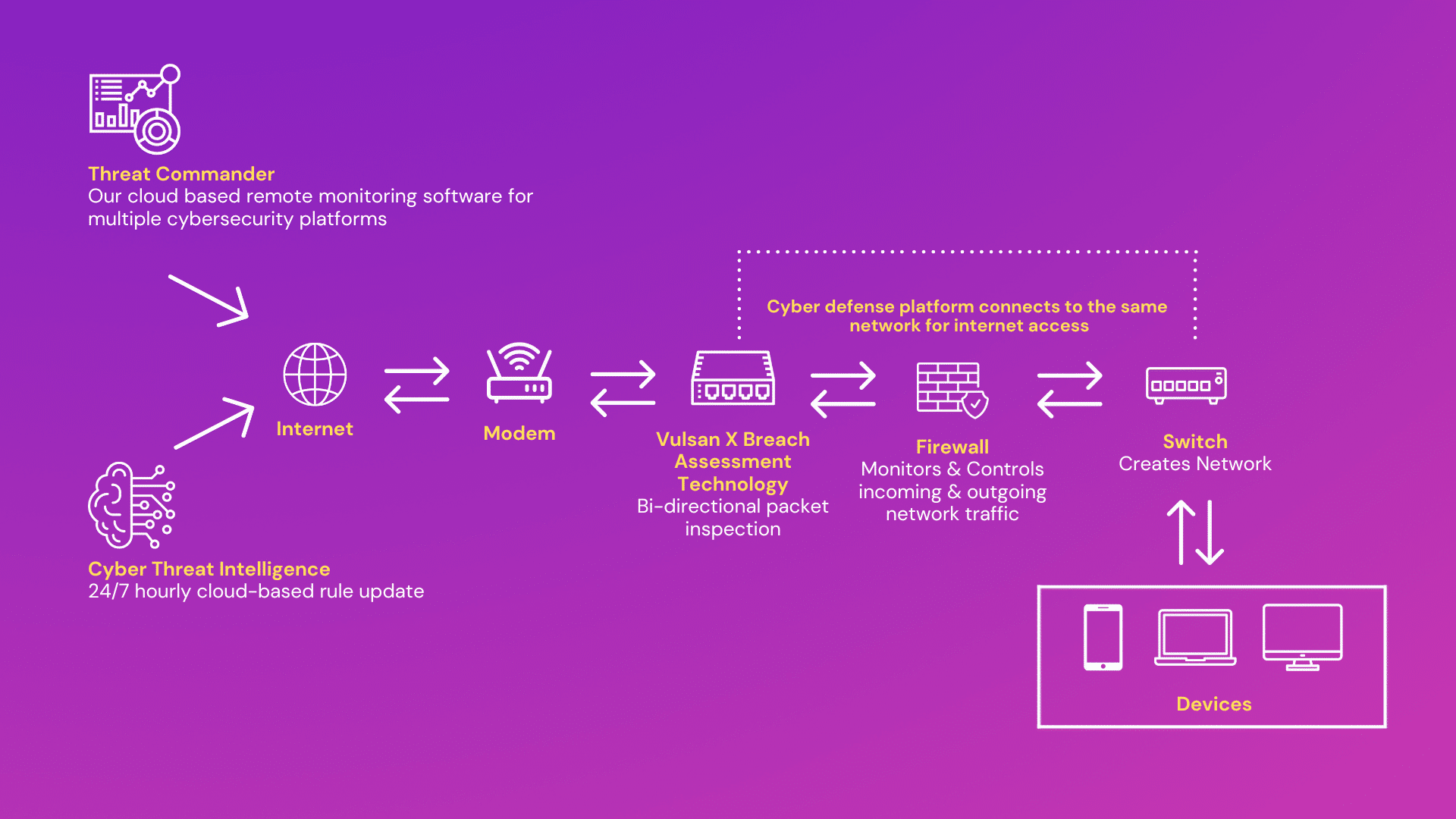

A Threat Command Center (TCC) is a facility or operational unit that serves as a central hub for monitoring, assessing, and responding to potential threats or security incidents. It is typically used in the context of security, defense, or emergency management.
Threat Command Center is responsible for gathering real-time information from various sources, such as surveillance systems, sensors, intelligence agencies, and other data feeds. It analyzes the data to identify potential threats, vulnerabilities, or abnormal activities that may pose risks to an organization, community, or critical infrastructure.
The command center coordinates response efforts, communicates with relevant stakeholders, and implements necessary actions to mitigate or address the identified threats. It may involve collaboration among different agencies, security personnel, law enforcement, and emergency services.
The primary goal of a Threat Command Center is to enhance situational awareness, enable effective decision-making, and facilitate timely responses to ensure the safety and security of assets, people, or critical operations.
1. Early Threat Detection
A threat command center is equipped with advanced monitoring tools and technologies that continuously analyze network traffic, system logs, and security alerts. This enables early detection of potential threats and vulnerabilities, allowing security teams to take immediate action.
2. Rapid Incident Response
With a dedicated team of security professionals and the ability to monitor security events in real-time, a threat command center enables swift incident response. Security analysts can quickly assess and prioritize threats, contain and remediate security incidents, and minimize the impact of breaches.
3. Centralized Threat Intelligence
A threat command center serves as a central hub for collecting, analyzing, and sharing threat intelligence. It consolidates information from various sources such as threat feeds, security vendors, industry reports, and internal incident data. This centralized intelligence helps security teams stay up-to-date on emerging threats and adopt proactive security measures.

